Amazon Athena
The first thing you’ll need to do is create an IAM user that will have permissions to run queries with Amazon Athena and access the S3 buckets that contain your data.
Create IAM Policy
The policy should allow access to your S3 bucket
- Sign in to the IAM console at https://console.aws.amazon.com/iam/.
- In the navigation pane, choose Policies, and then Create Policy.
In the policy body, you can use a policy similar to:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::Your_Bucket_Name/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::my-bucket"
]
}
]
}
Don’t forget to change Your_Bucket_Name to your bucket name. You can list several buckets, but please note that we have separate permissions for the bucket ( arn:aws:s3:::my-bucket) and the objects (arn:aws:s3:::my-bucket/*).
Create IAM User
- Sign in to the IAM console at https://console.aws.amazon.com/iam/.
- In the navigation pane, choose Users, and then Add User.
- Enter the desired User Name.
- Check the checkbox next to Programmatic Access and then click Next.
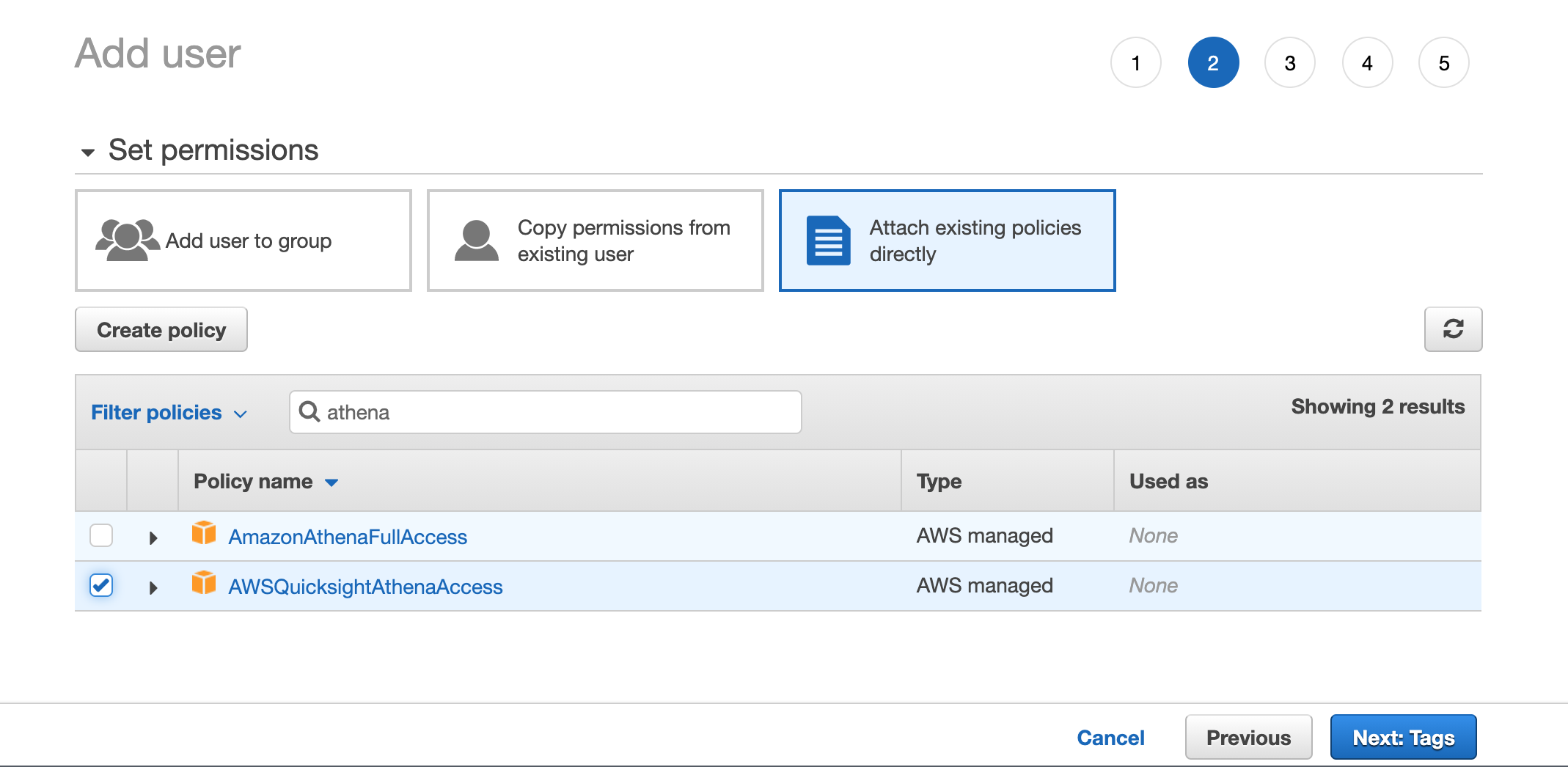
- In the Permissions step, select Attach existing policies directly and attach the AWSQuicksightAthenaAccess policy along with the one to access S3 buckets you created previously.
- Click Next, then review all the details and Create User.
- Take note of the Access Key ID and Secret Access Key.
Create Athena Data Source
In Cast, in the New Data Source page select “Athena” as the data source type and fill out the details using the information from the previous step:
- AWS Access Key and AWS Secret Key are the ones from the previous step.
- AWS Region is the region where you use Amazon Athena.
- S3 Staging Path is the bucket Amazon Athena uses for staging/query results, you might have created it already if you used Amazon Athena from AWS console - simply copy the same path.
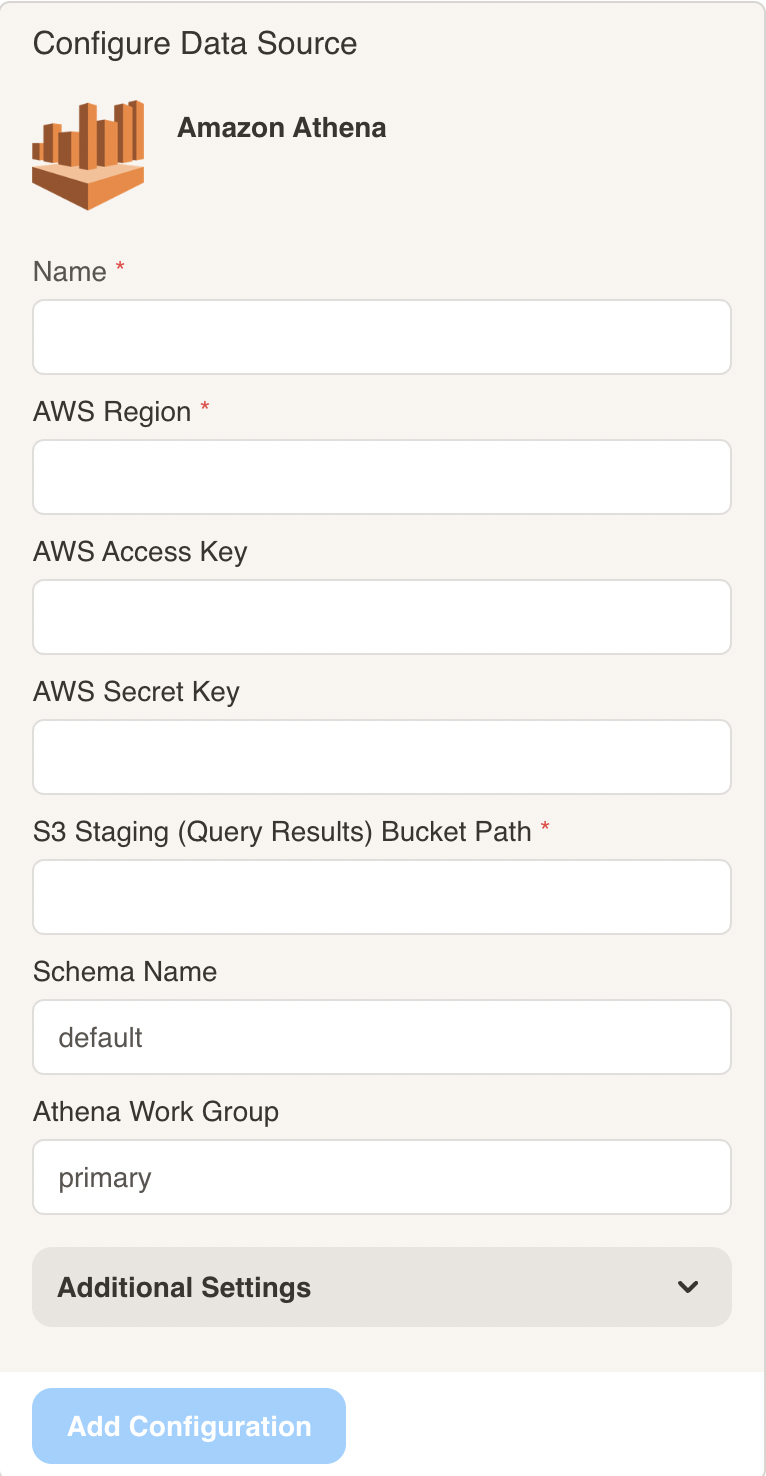
If you have trouble refreshing the Athena data source schema, check whether you’re using AWS Glue. If so you should toggle Use Glue Data Catalog under the Additional Settings menu.
Troubleshooting
AWSQuicksightAthenaAccess
When using Athena you need the following S3 permissions:
- Read permissions for the buckets you query from.
- Write permissions for the Query Results bucket.
The latter is supposed to be covered by the AWSQuicksightAthenaAccess policy, but it defines this only for the following buckets: arn:aws:s3:::aws-athena-query-results-* .
If you use a different bucket location, you need to specify it in your custom policy. The required permissions for the query results bucket are:
"s3:GetBucketLocation",
"s3:GetObject",
"s3:ListBucket",
"s3:ListBucketMultipartUploads",
"s3:ListMultipartUploadParts",
"s3:AbortMultipartUpload",
"s3:CreateBucket",
"s3:PutObject"